Palo Alto Networks has disclosed a critical (CVSS10) command injection vulnerability in Global Protect Gateway, which is the VPN component of PAN-OS powered networking appliances.
The vulnerability affects only self-hosted versions as shown in the manufacturer provided table below.
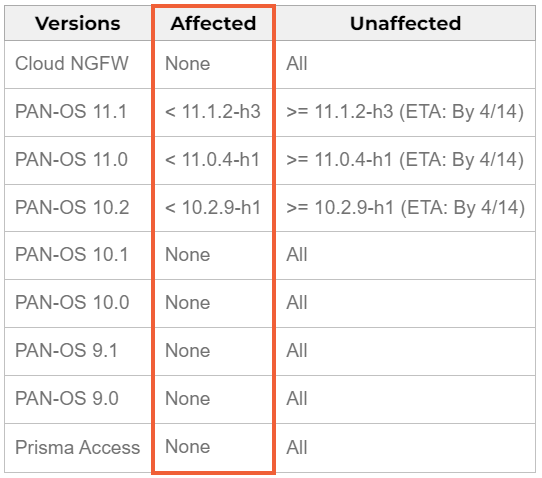
Affected devices must match the PAN-OS versions shown above, and in addition must have Global Protect Gateway and device telemetry enabled. These can be verified through the firewall web interface (Device > Setup > Telemetry).
The vulnerability is categorised as an improper neutralisation of elements used in a command under Common Weaknesses Enumeration number 77.
Palo Alto has issued the following guidance to potentially affected customers:
Recommended Mitigation: Customers with a Threat Prevention subscription can block attacks for this vulnerability by enabling Threat ID 95187 (introduced in Applications and Threats content version 8833-8682).
In addition to enabling Threat ID 95187, customers must ensure vulnerability protection has been applied to their GlobalProtect interface to prevent exploitation of this issue on their device. Please see https://live.paloaltonetworks.com/t5/globalprotect-articles/applying-vulnerability-protection-to-globalprotect-interfaces/ta-p/340184 for more information.
If you are unable to apply the Threat Prevention based mitigation at this time, you can still mitigate the impact of this vulnerability by temporarily disabling device telemetry until the device is upgraded to a fixed PAN-OS version. Once upgraded, device telemetry should be re-enabled on the device.
Please see the following page for details on how to temporarily disable device telemetry: https://docs.paloaltonetworks.com/pan-os/11-0/pan-os-admin/device-telemetry/device-telemetry-configure/device-telemetry-disable.
Integrity360 strongly recommends all Palo Alto Networks customers review their estate to check for the presence of appliances with these versions and feature configurations as exploitation of this vulnerability will allow threat actors to enter the network. There are reports that this vulnerability has already been exploited in production systems.






