Very few of us have experienced times like this in our lifetime. A global invisible threat to our lifestyle, our economics, our health and our very existence in some cases, has filled our daily lives.
There’s a variety of “new normal” that comes with it. Shaking hands; taking public transportation; going to dinner. The very face-to-face connections that we as humans crave. Our work, where possible, has transformed. It’s now done remotely, over the internet or phone, and always at a safe distance.
However, this is not another Covid-19 filled article about the issues of today. It’s a brief glimpse into what the future might hold – the transition to a new norm. We may not travel the same way again and we might not work the same way again, but the challenges of securing our organisation and protecting our personal data will remain.
It will change, it will evolve and we need to be ready. Now may be the ideal opportunity to reset our data protection and security activity priorities.
The Comfort Zone
There’s a graphic commonly used in training that explains the Comfort Zone we all like to remain in. It’s the zone where we feel safe and in control, and it changes based on our personal growth and development. The more that we extend our Comfort Zone, the better chance we have to conquer previously insurmountable goals.
It’s a model that I’ve tried to adapt to information security to help organisations find a path through these times when it comes to their data protection posture.
The new norm of data protection and information security begins outside your Comfort Zone
Your Comfort Zone is a place where you feel in control. You are maintaining your control environment as it was six months or year ago. It’s your psychological state where you are familiar with your surroundings.
However, your comfort zone may also be hindering you, your team’s and your organisation’s progression and development in the challenging times we are experiencing and what lies ahead. Relying on your current control posture will not assist your organisation stay protected while your business is rapidly evolving. Activities undertaken in previous years or months, such as mis-targeted awareness, inappropriate metrics or endless workbook questionnaires, will become quickly outdated and not provide the protection level required.
The visual below represents how evolving your approach to security and data protection from the Comfort Zone can be a step towards reshaping the future focus of data protection and information security activities. The four zones in this diagram include: Comfort Zone, Fear Zone, Learning Zone and Growth Zone.
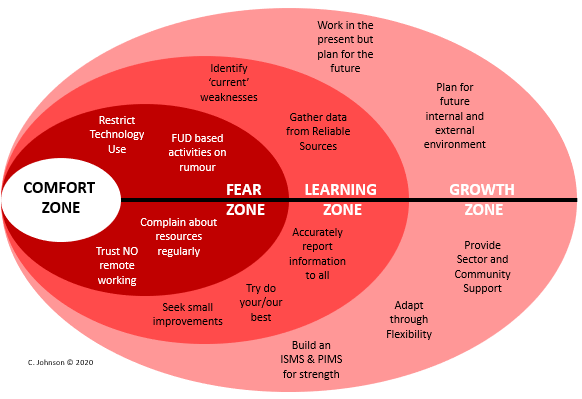
The current pandemic places organisations and individuals in an unfamiliar situation with new pressures and new stresses, and we may not feel in control. This may lead us into the Fear Zone. This may leave us with a low confidence level, high stress level and a desire to return to the Comfort Zone. What we fail to realise is that this zone is temporary and if navigated carefully we can have an improved environment and mindset.
Each zone represents progress towards achieving a new security and data protection model for your organisation as we begin the transition from the current situation. Most organisations are satisfied to remain in the Comfort Zone. The control environment fits like an old pair of slippers: they’re warm, comfortable and reassuring. However, they may be wearing thin underneath.
If you and your organisation can find the courage and belief you can progress to the Learning Zone. The Learning Zone is where we can start to enhance information security, evaluate our own strategy and our organisation’s approach, and eventually evolve into a stronger individual, team and organisation.
Reaching the Growth Zone can be challenging and requires resilience and maybe even assistance from others to ease the change and evolvement. By moving through the zones to the Growth Zone we can achieve a stronger security and data protection posture based on accurate data with strong links to your organisation’s needs. You will obtain efficiency in a focused control environment that is flexible, scalable and suitable for the new norm.
Fear Zone
Here’s how to identify if you’re currently in the Fear Zone
- Restrict Technology: Your business implements stringent controls in a knee-jerk fashion that do not allow for temporary use of new technologies that may enable the business to remain in business. A good example is Zoom. It has issues with security and the protection of data. However, it has allowed dispersed teams to connect, to maintain the company community atmosphere that is key to staying in business. Do your research, communicate the safest way to use new tools and support the organisation’s community
- FUD based activities based on rumour: You base communications that warn employees or perform risk reporting based on unverified sources such as social media, which isn't healthy for your organisation
- Complain about resources regularly: During this time we are all under pressure. Some are being redeployed into new areas that may not fully understand. Constantly complaining about resources when the business needs our support will not gain support for our activities when we need them most. Identify the right time to raise the appropriate concern
- No trust with remote working: You secure the use of remote working in such a restrictive manner that WFH becomes a challenge in which the business cannot maintain current operations.
As mentioned, this zone is temporary. Be careful of any FUD based decisions. Seek the support of senior management and work with all business areas to operate in a secure and data protection compliant manner.
Learning Zone
Here’s how to move into the Learning Zone:
- Identify ‘current’ weaknesses: Your risk register may have gone out of date as soon as the pandemic controls were implemented. This is an opportunity to learn where your new weaknesses may be
- Gather data from reliable sources: Every media outlet is filled with Covid-19 related news. Social media is a constant stream of it. Pick and choose reliable sources for any guidance you are going to rely on for activities, communications or assessments
- Accurately report information to all: Following on from gathering from reliable sources, you should ensure your communications are factual, concise and relevant to your audience. Senior management will want to be reassured that the organisation is operating securely. Remote workers will seek guidance and reassurance on how to work
- Try your best and seek small improvements: We can all only try our best in these current times. Do not try and over stretch your team or yourself. We have other important concerns. Support each other and look after your physical and mental health. Without these, we cannot help our organisations protect their data and assets.
The opportunities to transition to the new norm start here. Learn to operate efficiently in your new environment. Accurately communicate. Make small improvements on the new challenges. Look after yourself and your team.
Growth Zone
Ultimately, you want to make your way to the Growth Zone – which involves a mix of:
|
|
|
|
|
|
|
|
|
Growth activities should be geared towards building a strong, secure organisation. While continuing to maintain current activities, it’s important to establish what the Information Security Management System (ISMS) and the Personal Information Management System (PIMS) will look like in the coming months and years when the pandemic controls start to lift. Will your organisation face new challenges outside the return of business economically?
To identify this, ask yourself questions like:
- Will a significant part of the workforce now seek to give up on the daily commute and WFH? This could give rise to a new ‘Remote Working Framework’ for your organisation and/or new baselines for handling personal data.
- Did your organisation have the resources to maintain security and data protection activities during the pandemic when a resource was unavailable? Growth in the use of flexible ‘virtual’ security or data protection professionals is expected as they are considered as a control for future BCP or Pandemic Plans
- Was the organisation ready for the risks it faced? Implementing a three-year cyclical threat landscape analysis will assist organisations in being better prepared for any future challenges from varying sources
Is now the right time?
It may be difficult at this stage to see beyond the current situation. However, I believe that this is an opportunity to define a new norm in our society, our organisations and individually. It’s time to embrace new ideas and practices where the sky is the limit.
The first step to help break out of the Comfort Zone will be the hardest. Start with small steps. Switch some of your normal security and data protection practices. Have flexibility. Have empathy for others. Believe in the process. The benefits for you and your organisation are there to be had.
This blog and its content are provided as a general guide to the subject matter. You should always seek specialist advice about your specific situation – no two organisations are alike.





