The global WannaCry Ransomware pandemic is still making headline news and has been well covered by news and tech media outlets. The security teams at Integrity360 have been following analysis & updates closely, from both our industry partners and the wider security community, and working with our customers around the clock to improve their security posture and close any avenues of attack in light of WannaCry.
This update provides a summary of the pertinent details, new developments, our short term expectations and the current recommendations.
Current Status
As detailed in our initial advisory progress of the original variant was slowed drastically when a malware researcher registered the kill switch domain and sinkholed the traffic. It is very important to note that this action would only have an impact in your network as long as the infected devices have free access to the domain. The malware is not Proxy aware and in networks where an explicit proxy is used, it will not be able to connect to the sinkhole without additional changes (killswitch and proxy). For this reason we expect the infection numbers to continue to rise come Monday morning, once users start opening their inboxes.
At the time of writing almost 200,000 infections had been detected in 150+ countries, and 66,000 new infections in the last 24 hours:
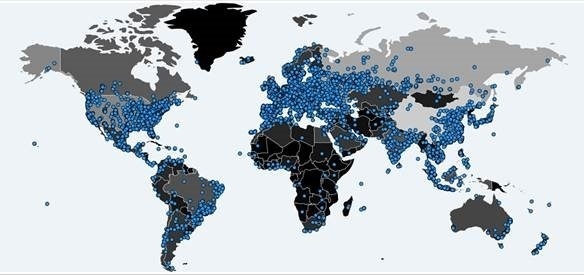
New Strains
A number of new strains of WannaCry have been detected and reverse engineered by malware researchers. There new strains attempt to circumvent the sinkhole by changing the kill switch URL. Presently these are considered patched or modified versions of the original, by copycat attackers using hex editors, rather than being completely re-written by the original authors. The newly detected URLs have been added to the current sink hole. In one case the kill switch check has been completely removed via hex editor but this sample provided to be corrupt and failed to encrypt files.
As it is relatively easy for an experienced hacker to modify the binary there is a very real fear multiple attackers may take advantage of the situation over the coming days whilst systems are still unpatched.
Although at this stage we have only seen altered versions of the original malware, it is highly expected that the original authors will release an entirely new version of the malware with the kill switch removed in the coming days. It is expected that this version will be modified to avoid newly created anti-virus signatures, allowing it to exploit vulnerable systems and repeat the “success” of the original version. There is also concern other NSA leaked exploits may be combined with WannaCry or other forms of ransomware in near future.
Payment
It is strongly recommend that you do not pay the ransom. Analysis of the malware, and its payment method, show it is either not created with decryption in mind, or the payment & decryption process is simply poorly written. Unlike other ransomware there is no automated association of payment to a unique host ID to allow the decryption keys to be provided automatically on payment. One piece of analysis also indicated decryption would potentially be a manual process, interacting with the attackers, via the Tor network, which would be impossible for all 200,000 infected hosts. https://modexp.wordpress.com/2017/05/15/wanacryptor/
At the time of writing there have been $33,000 sent to the 3 bitcoin wallets used in the attacks and no successful payment/decryptions have been reported.
Current Recommendations:
- Apply the latest Windows patches to all servers and workstations. In particular, apply the patch for MS17-010. This should prevent the infection spreading should one of your systems be infected.
- Microsoft has released patches for unsupported systems such as Windows Server 2003 and Windows XP. It is highly recommended you patch these systems - https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
- Disable SMBv1. The element used to self-propagate the malware exploits a vulnerability in SMBv1. Disabling SMBv1 will prevent the malware spreading in the environment
- Instruction on how to disable SMBv1 can be found here: https://support.microsoft.com/en-us/help/2696547/how-to-enable-and-disable-smbv1,-smbv2,-and-smbv3-in-windows-vista,-windows-server-2008,-windows-7,-windows-server-2008-r2,-windows-8,-and-windows-server-2012
- Ensure firewall policies block inbound SMB connections from the internet and 3rdparty VPNs (TCP ports 137/139/445).
- Where SMB is explicitly required through the firewall for business reasons ensure the server is either patched, has SMBv1 disabled or, as a last resort, ensure the traffic traverses an IPS with the relevant protections enabled.
- Where systems cannot be patched or SMBv1 disabled Integrity360 highly recommends isolating these systems in the network, or removing from the network entirely.
- Advise users to be extra vigilant when receiving emails. Any emails with suspicious links or attachments should not be opened and links should not be clicked. In the short term, it may be prudent to send any emails with attachments to quarantine and release on a manual case by case basis.
- Check integrity of backups and ensure that stored in a non-network accessible locations, and that the server is patched or SMBv1 disabled.
- Update all IPS signatures and monitor for new updates. The majority of major IPS vendors released signatures for the SMB vulnerabilities (CVE-2017-0143 to CVE-2017-0146 & CVE-2017-0148) back in March. Please ensure these are set to Block/Prevent. Please note, these will only be effective at preventing the spread of any infection and where the LAN environment is segmented and internal traffic passes via an IPS
Please email info@integrity360.com if you would like further advice on protecting against this threat.
References
- Check Point Threat Intelligence and Malware Research Team - http://blog.checkpoint.com/2017/05/14/wannacry-paid-time-off/
- Wcrypt Tracker - https://intel.malwaretech.com/botnet/wcrypt/
We would like to acknowledge our partners, Check Point for their information, analysis and assistance in compiling this article.





