According to the government's Cyber Security Breaches Survey 2023, phishing is the most common form of cybercriminal activity suffered by UK businesses and charities, with 79% having been targeted by phishing scams.
There are several tactics employed, but all have the same objective; to trick users into doing something that could harm their business. Whether it’s a spray and pray campaign or a targeted phishing attack, the stats don’t lie when they reveal that phishing is still costing the global economy billions in financial losses. That is why we have created a phishing guide to help outline the most common themes of this malicious form of social engineering.
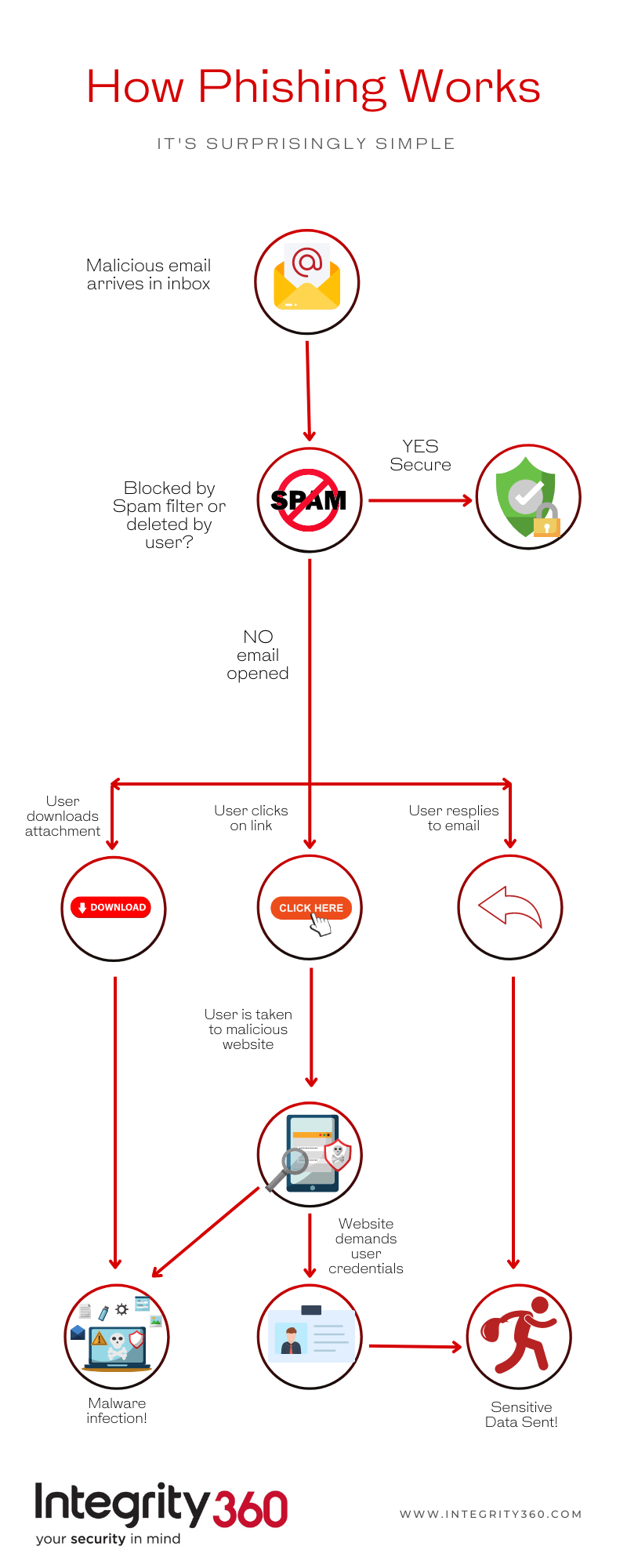
How Phishing Works
Phishing is one of the most common forms of cyberattack. 91% of corporate phishing attacks are display name spoofs, meaning that the average business end user faces at least one risky email per day.
Phishing Guide - The Different Types
Phishing - The most common type of phishing sees a scammer cast their net far and wide in the hopes of landing a fish (i.e., you). These are typically mass-mailed and sees the attacker pretending to be someone they are not and tries to trick the recipient into doing something, such as logging on to a dodgy website or downloading malware.
Spear Phishing - Spear Phishers are likely to send their victim’s personalised emails that are associated with either someone they know or perhaps a company they’ve done business with. Because the email appears to be from someone the target knows, they are less likely to be vigilant and far more likely to give the attacker exactly what they want.
Spear phishers are targeted attempts to find out as much about their victims as possible. They do this by scouring the internet for information in a tactic called Social Engineering. By the end of their reconnaissance period, they will likely know your email address and perhaps a little bit about your personal life thanks to your social media accounts.
Imagine all the things you’ve posted on social media over the years; if your social media accounts are wide open, then a phisher can easily find out a lot about you. They can easily learn who your friends are, what businesses you use and the things you like.
If you receive an email that claims to be from a colleague or superior asking for urgent action to be taken, cybercriminals are betting that you will feel pressured to act before thinking. Always check with the person the email claims to be from to make certain it is legitimate.
Whaling- Whaling is a type of phishing attack that targets an organisations leader (the big fish) or executives. A whaling attack is also known as a C-level fraud. A scammer will do reconnaissance on the business they’re hoping to scam and will aim to learn how an organisation’s emails look and how they are structured in order to make the phishing email as believable as possible.
If the scammer opts to pose as the CEO or senior executive, they will target employees lower down the structural chain and ask them to transfer sensitive data or money into an account of the attackers choosing.
Posing as an executive is an effective tactic as most employees don’t want to disappoint their senior management and will often carry out the order without question. In most cases an employee, no matter how odd the request may be, will want to make a good impression and not disappoint their employer.
Whaling emails often ask employees to keep things confidential and bypass normal approval channels so employees should always double check and confirm that any unusual requests are legitimate. Calling to confirm requests should be adopted as policy.
 Business email compromise (BEC) - In BEC attacks criminals target key individuals in an organisations finance and accounting departments. They do this by posting as a financial officer or CEO in order to put pressure on employees into making money transfers to unauthorised accounts. A criminal can spend a long-time lurking and watching an executive’s email activity in order to learn how the company does things.
Business email compromise (BEC) - In BEC attacks criminals target key individuals in an organisations finance and accounting departments. They do this by posting as a financial officer or CEO in order to put pressure on employees into making money transfers to unauthorised accounts. A criminal can spend a long-time lurking and watching an executive’s email activity in order to learn how the company does things.
BEC scams are a big issue. In a March 2022 report, the USA’s Internet Crime Complaints Centre (IC3) said that it had received close to 20,000 BEC complaints throughout 2021, with estimated adjusted losses of roughly $2.4 billion. Meanwhile, in the UK over 6,000 UK businesses are targeted every month. The frequency of such attacks makes the UK one of the most targeted countries in the world.
Cloning- Cloning is a type of phishing attack that sees a legitimate and previously delivered email that contains a link or attachment being taken by a scammer and used to create a copied fake email. These emails are designed to get under the radar by appearing to be genuine and can be tricky to spot.
Vishing- Not all forms of phishing attacks come in the form of emails or electronically at all. In the case of Vishing, fraudsters make phone calls or leave voice mail messages claiming to be from a reputable source. They do this to trick or pressure a victim into revealing sensitive personal information such as credit card numbers or bank details. Often, the scammers will attain phone numbers from other data breaches or just search the phone book or glean the info from social media or business websites.
Smishing- Smishing is just another form phishing except the attacker sends text messages containing malicious links rather than emails. With more people owning a smart phone than ever before the number of smishing attacks has increased dramatically in the last few years.
QR Code Phishing- With virtually every company adopting and utilising QR codes for a wide range of purposes it is not much of a surprise that cyber criminals have realised that they can be used for phishing attacks. This form of attack works in much the same way as email or SMS based attacks in that the attacker will try to dupe a victim into using a compromised QR code that will take them to a malicious site. In some cases, attackers have used QR code phishing on things such as parking tickets and parking meters.
It’s everyone’s job to defend against Phishing
Employees at all levels of the business can be an effective “human firewall” against phishing and spear-phishing attempts when given the right resources.
Working with a Cyber Risk and Assurance (CRA) team can help your company:
- Develop a comprehensive strategy that intertwines technology with the human element of cyber security.
- Build an employee awareness training program
- Identify a framework that fits the enterprise's unique risks and requirements (NIST, CIS Top 20, COBIT, ISO 27001, etc.).
- Map the digital environment to understand what sensitive data should be a priority to protect and how to control access to it.
As phishers’ tactics evolve, so should your business’ ability to detect and defend against them. Contact an Integrity360 advisor to learn more.







