Hacking-as-a-Service: Crimeware emerging as a pay-to-play threat
Hacking-as-a-Service: Crimeware emerging as a pay-to-play threat
Our Managed Detection and Response Services provide continuous monitoring from a team who’ll neutralise any breaches at speed...
Gain access to malware experts to quickly contain threats and reduce future exposure to attacks...
Integrity360 has been recognised as a Gartner Representative Vendor.
Many organisations are choosing CyberFire MDR to strengthen their defences. Discover how it can protect your business in our brochure.
Cyber attacks often seem faceless, but hidden behind the headlines of financial loss and technical details there are very real human stories.
In 2025, we’re witnessing a shift in how ransomware operates, who it targets, and the consequences of falling victim.
Stay ahead of the latest cybersecurity industry developments, advancements and threats, and understand how you can best protect your organisation.
Do you know what your company’s network vulnerabilities are? Businesses that invest in penetration testing do.
If your business handles credit card data, PCI DSS compliance isn’t optional—it’s critical. From retailers and e-commerce platforms to service providers and financial institutions, securing credit card data is critical to customer trust and preventing fraud.
Stay informed with the latest cybersecurity news with our weekly threat roundups.
Confused about cybersecurity? Our A-Z Glossary of terms can help you navigate this complicated industry.
For many small and mid-sized businesses, cybersecurity can feel overwhelming.
SOC 2 certification reflects Integrity360’s continued investment in strengthening cyber resilience for clients across highly regulated and high-risk industries.
Leading Canadian cybersecurity services provider Advantus360 joins Integrity360 creating the group’s first hub in North America
Posts about:

Hacking-as-a-Service: Crimeware emerging as a pay-to-play threat

Last Updated: 08/01/2018 10.00

Last updated: 31/10/2017 11:00
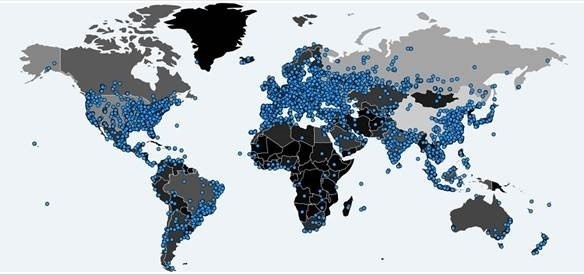
The global WannaCry Ransomware pandemic is still making headline news and has been well covered by news and tech media outlets. The security teams at Integrity360 have been following analysis & updates closely, from both our industry partners and the wider security community, and working with our customers around the clock to improve their security posture and close any avenues of attack in light of WannaCry.
This update provides a summary of the pertinent details, new developments, our short term expectations and the current recommendations.
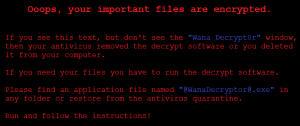
Please note that we have issued an updated advisory. (15/05/2017)

A vulnerability has been discovered in Windows 2003 Servers running IIS (Internet Information Services) 6.0. The exploit code takes advantage of a function within the WebDav service, allowing remote attackers to execute arbitrary code. Microsoft declared Windows Server 2003 end of life as of July 14, 2015, meaning no security patches will be released for the operating system.

Critical vulnerability discovered in Magento eCommerce software. Has been given a 9.8/10 in terms of severity due to unauthenticated remote code execution. CVE assigned is CVE-2016-4010.

DROWN is a serious vulnerability that affects HTTPS and other services that rely on SSL and TLS, some of the essential cryptographic protocols for Internet security. These protocols allow everyone on the Internet to browse the web, use email, shop online, and send instant messages without third-parties being able to read the communication.

Cisco released a patch for a critical security vulnerability affecting its Internet Key Exchange version 1 (IKEv1) and version 2 (IKEv2) of ASA software, the operating system that runs the company's Adaptive Security Appliance security devices. The flaw allows attackers to remotely execute code or reload affected systems and take over Adaptive Security Appliance (ASA) firewalls.

Integrity360 has today released the following advisory in relation to a recent upsurge in DDoS attacks. We’d like to encourage our clients to review this advisory and action as required.

The recent issue that was disclosed publicly was resolved and a patch was made available in July 2014 as part of Fortinet's commitment to ensuring the quality and integrity of their codebase. This was not a “backdoor” vulnerability issue but rather a management authentication issue. The issue was identified by Fortinet's Product Security team as part of their regular review and testing efforts.

Administrative Access (CVE-2015-7755) only affects ScreenOS 6.3.0r17 through 6.3.0r20. VPN Decryption (CVE-2015-7756) only affects ScreenOS 6.2.0r15 through 6.2.0r18 and 6.3.0r12 through 6.3.0r20.